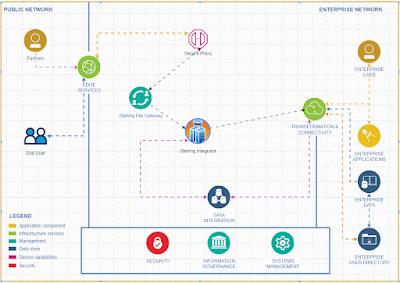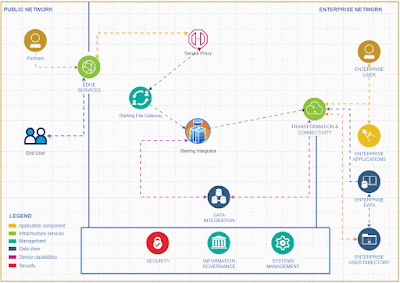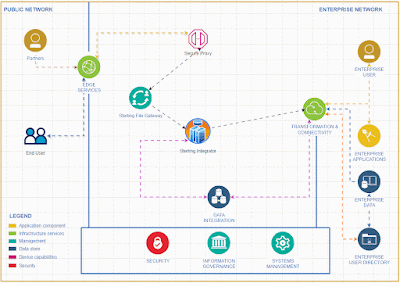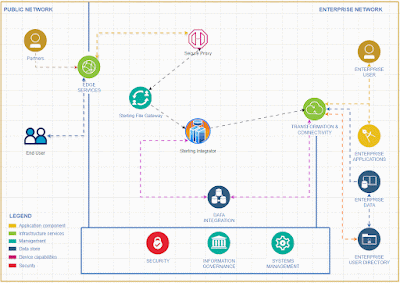
To activate and integrate the rate limiter feature in Sterling Integrator for comprehensive API functionality, follow these steps.To effectively deliver a service, it's essential to create a system that accepts input from clients and returns the appropriate output based on that input.
When we offer this service, it's important to pinpoint the client's IP address for any requests originating from outside our network.
To achieve the capability of identifying the client IP address within Sterling Integrator, we should adhere to the following steps.
To activate the Client IP feature, follow these steps: First, include the property client_ip_correlation_enabled=false in the jdbc.properties_platform_ifcbase_ext.in file.
Next, execute ./setupfiles.sh.
This feature captures the IP address of the client that initiates the request.
Certain clients require this functionality to comply with regulatory standards.
Before you enable the Client IP feature, ensure that your firewall is configured to permit the IP address to pass through the Sterling External Authentication Server.
We will now verify the available rate limit for the customer associated with the given IP address.
As developers, we will save this information in our database. Each time a request is received, we will assess the rate limit for that partner.
If the request falls within the allowed rate limit, it will be forwarded to the appropriate API service.
Additionally, we can implement another check to monitor the number of requests made by the partner within a defined time frame. For instance, we could allocate a limit of 1,000 requests per hour for a specific partner based on their IP address.
To put this into action, we will track the number of requests made by the partner.
If any conditions fail, we will provide the relevant error code and description to the partner. They will need to rectify the issue by upgrading their subscription with the service provider.
When we integrate this functionality into Sterling Integrator, we can incorporate rate limiting within a generic process. If the result is positive, the request will then be directed to the appropriate API service business process.
I recommend implementing API capabilities in Sterling Integrator rather than using specific API tools for small and medium business who is already using Sterling Integrator for their EDI integrations .Given the business capacity, Sterling Integrator can effectively expose API services to the external world. It offers robust error handling features and a clear understanding of error codes, making it particularly suitable for small and medium-sized businesses.
The Sterling Integrator Server offers enhanced functionality, equipped with a wider array of services and adapters, allowing us to implement simple functions without the need for coding.
Tracking requests and generating reports is a breeze with the Sterling File Gateway.
While this tool primarily focuses on managing EDI-based transactions, it can also be effectively utilized for API service implementations.
There is a wealth of Sterling technical resources available in the market.
One important consideration when using Sterling Integrator as an API endpoint is that it only supports XML-based transactions and requests, excluding JSON format. To address this limitation, we can create an alternative solution by leveraging the Java Task Service to develop a Java program that formats JSON.
1. One minor limitation of the API toolscurrently on the market is that implementing any functionality requires coding in a language chosen by the organization or developer.
Maintaining this code can also pose challenges within the organization.
Should there be any updates or changes to the service in the future, it may necessitate hiring new personnel with expertise in the original programming language or rewriting the functionality in a different language altogether.
Additionally, as a centralized access point, an API serves as a gateway that can attract the attention of hackers. If an API is breached, it can expose all connected applications and systems to potential threats.